Hackers have been hijacking well-known YouTube channels since at least 2019. Sometimes they spread cryptocurrency scams, and sometimes they just auction off access to accounts. Now, Google has detailed the techniques it hired hackers to hack thousands of YouTube creators over the past few years.
It all started with a phishing scam. The attacker sends an email to the YouTube creator that appears to be from a real service, such as a VPN, a photo-editing app or an antivirus product, and offers to work with it. They came up with a standard promotional arrangement: show our product to your audience and we’ll pay you a fee. It’s an everyday deal for YouTube celebrities, a bustling industry filled with Internet celebrity bonuses.
Clicking on a link to download the product, however, takes the creator to a landing site for malware rather than the real deal. In some cases, hackers impersonated known numbers like Cisco VPNs and Steam games, or pretended to be media organizations focused on COVID-19.
Google said they has found more than 1,000 domains created specifically to infect unsuspecting YouTubers. The company also found 15,000 email accounts linked to the attackers behind the attack. These attacks do not appear to be the work of a single entity, instead, various hackers advertised account takeover services on Russian-language forums, Google said.

Once a YouTuber inadvertently downloads the malware, it grabs specific cookies from their browser. These “session cookies” confirm that the user has successfully logged in to their account. Hackers can upload stolen cookies to malicious servers, allowing them to impersonate authenticated victims. Session cookies are particularly valuable to attackers because they eliminate the need for any part of the login process.
The technique has been around for more than a decade, and Google says it has observed hackers using about a dozen different off-the-shelf open-source malware tools to steal browser cookies from victims’ devices during these activities.Many hacking tools can also steal passwords.
“Account hijacking attacks remain a rampant threat because attackers can exploit affected accounts in multiple ways,” Polakis said.”Hacked email accounts can be used by attackers to spread scams and phishing campaigns, and even stolen session cookies can be used to withdraw funds from victims’ financial accounts.”
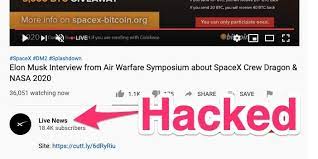
In August 2020, hackers hijacked multiple accounts with hundreds of thousands of followers, changed the channel name to “Elon Musk” or “Space X,” and broadcast the Bitcoin gift scam live. It is unclear how much revenue these attacks generate, but given how common they have become, they have been at least moderately successful.
So far, Google says it has found more than 1,000 domains created specifically to infect unsuspecting YouTubers. The Company also found 15,000 email accounts linked to The Instruction behind The Attack.
While two-factor authentication does not prevent these malware-based cookie thefts, it is an important protection against other types of scams and phishing. Starting November 1, Google will require creators of YouTube channels to turn on two features for their YouTube Studios or Google accounts associated with YouTube Studios Content Manager. It’s also important to note Google’s “safe viewing” warning about potentially malicious pages.
As always, be careful what you click on and what attachments you download from your email. The advice for YouTube viewers is even simpler: If your favorite channel is promoting a cryptocurrency deal that seems too good to be true, give it a Dramatic Chipmunk perspective and move on.
No Comments Yet