
There is a historic tendency for tech enthusiasts to overstate the importance of the latest digital wizardry during major global conflicts. Remember Iran’s “Twitter Revolution?” That’s not to ignore tech’s impact. Scholars will debate the role of disinformation during our time for decades. I find Carole Cadwaller’s discussion of the first Great Information War, which she says began in 2014 during Russia’s first invasion of Ukraine, compelling. Still, plenty of tech analysts and sales agents sitting behind keyboards stand to gain a lot by inserting themselves into the middle of a war from a comfortable distance. When there are real bullets, bombs, and blood, I think it’s really important to keep bits and bytes in perspective.
And so it is with cryptocurrency and the current invasion of Ukraine. Let’s not get carried away with this “crypto’s big moment” talk. In fact, if I were a blockchain speculator, I’d be nervous that cryptocurrency is could take a big step back into the shadows.
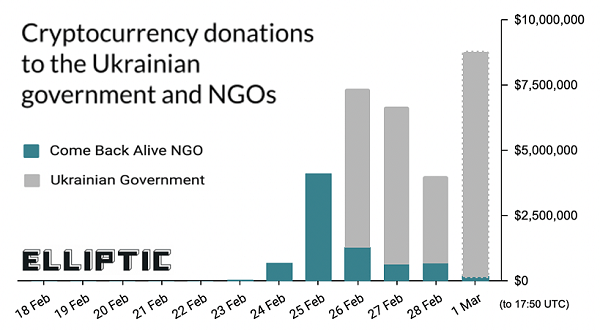
Crypto enthusiasts are having a hard time holding the company line that bitcoins=freedom when so many of them have been collected by Russians via ransomware. True, there are crypto donations headed towards Ukraine, but the greater use case seems to be evading international sanctions. Meanwhile, there is fear that cutting off Russian access to Western banking institutions would shove those transactions underground, into crypto-land. As exchanges debate how to handle this problem — cut off all Russian accounts? How would one even do that? — I asked a couple of leading critics what they thought the war means for the future of cryptocurrency. (Note: I am a visiting scholar at Duke University’s Sanford School of Public Policy).
Russia absolutely can and will use crypto to undermine and avoid U.S. sanctions. We know this because North Korea and Iran have already done it! While I agree that crypto’s limited use restricts its desirability, I am confident that U.S. sanctions on Russia will serve as an accelerate for broader crypto adoption. And when you’re talking about a nation-state, the question is not whether they can buy a coke with crypto, but whether they can store and transfer large amounts of wealth with it. And somehow, crypto has persisted as a store of value. We also know that Russia is the final destination for many ransomware payments, with Russian-based crypto exchanges willing to convert crypto to fiat. The only two cryptocurrency exchanges to be sanctioned by OFAC were in Russia.
See https://home.treasury.gov/news/press-releases/jy0364 and https://home.treasury.gov/news/press-releases/jy0471
Finally, I think it’s telling that the U.S. and our allies have yet to cut off Russian banks from SWIFT (Edit note: Some payments are slated to be cut off, but not all). There are several reasons for this, but the one left unsaid is that the administration worries this could accelerate Russia’s adoption of crypto.
The dollar’s status as the world’s reserve currency affords all Americans with tremendous opportunities (lower interest rates, easy travel, more commerce, etc…). It’s also allowed the U.S. government to leverage our financial system as an instrument of foreign policy. Crypto undermines all of this and once again I ask: what are we getting in return?
My take is that, unless the use of cryptocurrency is curtailed by the U.S. government: 1) Russia will seek to evade U.S. sanctions by transacting in cryptocurrency; and 2) Russia-based ransomware attackers will initiate a new wave of ransomware attacks. Here’s why:
First off, cryptocurrency use is not just well-suited to evade U.S. sanctions, its pseudo-anonymity is ideal for that purpose (and a broad range of other crimes).
Second, the key to sanctions programs is banks and KYC (know your customer) rules. Using cryptocurrency blinds banks and paralyzes AML (anti-money laundering) enforcement. Meanwhile, threat actors associated with rival nations such as Iran and North Korea have adopted using cryptocurrency (sometimes extorted via ransomware attacks) as a fast and easy means to bypass U.S. economic sanctions and funnel badly needed capital into their cash-starved economies. North Korea and Iran have already proven this notion by example. Indeed, per a United Nations Report, North Korea is using ransomware attacks to fund its nuclear program. Moreover, Iran reportedly uses bitcoin mining to evade sanctions and “export” millions of barrels of oil.
Third, we know already that Russia is the final destination for many ransomware payments, with Russian-based cryptocurrency exchanges willing to convert cryptocurrency to fiat. Thus, a profitable and successful ransomware attack revenue stream already exists for Russia. N.B. that though crypto exchanges in the U.S., Europe and Asia might (and that’s a big “might”) stop dealings with Russia (if that’s even possible), there are still some exchanges that are complicit in facilitating illicit activity, such as the Russian-based SUEX and Chatex services who were both sanctioned by the U.S. last year after facilitating more than $350 million in cryptocurrency transactions for Russia-based criminals. U.S. Treasury has already warned about these risks before, with officials pointing to an “explosion of risk” stemming from their use in terrorist financing and ransomware attacks and cautioning in October that cryptocurrencies “if left unchecked . . . could potentially harm the efficacy of American sanctions.”
Finally, Ransomware attacks have evolved into an extraordinarily successful tool for quickly raising cryptocurrency revenue — while also disrupting (sometimes significantly) the lives of U.S. businesses and citizens. Historically, ransomware attackers employed a type of malicious software designed to block access to a computer system or computer files until an extortion demand is paid. Now, in addition, by licensing their criminal wares to franchisees who can then orchestrate ransomware-as-service attacks, the threat is no longer merely the kidnapping of data but also the public release of that data via social media. To further pressure the victim, a ransomware attacker might even flood a website or network with more requests than it can handle by executing a distributed denial of service, or DDoS, attack, rendering the company inaccessible.
Indeed, the continuing success of ransomware attacks has spawned large, central, sophisticated cybercriminal organizations operating within a new and emerging criminal ecosystem consisting of an army of global threat actors using a dangerously evolving arsenal of high-tech intrusion appliances. Russia has, according to many reports, become the mothership of these organizations.
Extortion innovation is now an industry within itself as ransomware attackers have sharpened their business models, including guaranteeing turnaround times, providing real-time chat support for victims and offering payment demands customized to a victim’s financial profile. When it comes to ransomware attacks, there has perhaps never before in history been a crime that law enforcement seems so powerless to prevent, investigate, prosecute and bring to justice.
As an aside, please pay no attention to those spreading the myth that crypto-transactions will actually make it easier to impose sanctions because cryptocurrency trails are easy to trace. This is perhaps the most absurd, frustrating and entirely misleading of all crypto-enthusiast retort.
Bottom Line: Don’t count on Russian cyber-attackers to behave like the two Instagram celebrities DOJ recently arrested in NYC (and took six years to find) for money laundering in connection with a cyber-attack on Bitfinex. For dictatorial and rogue governments using ransomware attacks to extort cryptocurrency to use to replace their yachts, mansions and other ill-gotten assets, I would not expect search warrants and subpoenas (while certainly well-intentioned) to become any kind of panacea. Moreover, unless the U.S. takes action, the sanctions might even accelerate the use of cryptocurrency everywhere, ushering in an even more dangerous era of crypto-related cyber-crimes.
So What Should the U.S. Do Right Now About This Problem?
Curb the flow of bitcoin and other cryptocurrencies immediately.
Now that President Biden has created a cryptocurrency prosecutorial and investigative team, the next logical step is to sign an Executive Order to curtail the flow of bitcoin and other cryptocurrencies, making it challenging for Russia and other criminals to use cryptocurrencies to purchase U.S. goods and services. The Executive Order should:
- Prohibit any U.S. governmental entity from transacting in cryptocurrency and mandate that any entity that contracts with the U.S. government must attest that they do not engage in any transactions involving cryptocurrency; and
- Direct The Financial Crimes Enforcement Network of the U.S. Treasury (FinCEN) to require U.S. taxpayers holding more than $10,000 of cryptocurrency offshore to file FinCEN Form 114, known as the FBAR, to report these holdings (a proposal that FinCEN has already announced in 2020).
This kind of expeditious, efficient, inexpensive, straightforward and powerful approach could help deter the use of cryptocurrency to evade U.S. sanctions and help combat the many cyber-crimes that DOJ has cited as cryptocurrency’s most notorious abuses.
Though some experts seriously doubt it and some engineers specifically refute it or negate it, perhaps blockchain technology is more than a “glorified spreadsheet,” and will somehow become the most exciting, disruptive, transformative and efficiency enhancing breakthrough since sliced bread. If so, by rooting out cryptocurrency abuses via the powers of an Executive Order, President Biden could usher in a new era where blockchain and all of its purported promise can thrive, free from the onerous drag of its criminal exploitation.
I provide more detailed analysis and support for this executive order recommendation in an article I just wrote entitled, “What President Biden’s Crypto-Executive Order Should Say” and found here.


No Comments Yet